

In an era where cyber threats are omnipresent, small and medium-sized businesses (SMBs) need to take proactive steps to safeguard their digital assets. However, the landscape of cybersecurity can be daunting, with numerous frameworks, certifications, and regulations to consider. In this blog, we demystify these terms, explore their significance, and guide SMBs on implementing cost-effective cybersecurity measures that align with industry standards.
Frameworks provide a structured approach to cybersecurity, offering guidelines and best practices. Consider frameworks like NIST (National Institute of Standards and Technology) Cybersecurity Framework, which breaks down cybersecurity into five functions – Identify, Protect, Detect, Respond, and Recover. Adopting such frameworks helps SMBs organize their cybersecurity efforts cohesively.
Certifications validate that a business adheres to specific cybersecurity standards. Certifications such as ISO 27001, SOC 2 (Service Organization Control), and NIS2 (Network and Information Systems Directive) demonstrate a commitment to robust security practices. While attaining certifications may seem challenging, the investment pays off by enhancing the organization’s credibility and trustworthiness.
Regulations are legal requirements that businesses must comply with. The General Data Protection Regulation (GDPR) and Essential Eight from the Australian Signals Directorate are examples. SMBs should familiarize themselves with applicable regulations based on their industry and geographical location, ensuring they meet compliance standards.
Regularly updating software and systems is a fundamental cybersecurity practice. SMBs should establish a patch management process to address vulnerabilities promptly. Automated tools can simplify this process and ensure the business stays protected against emerging threats.
Efficient ITAM helps SMBs keep track of their digital assets, ensuring that all devices and software are accounted for. This is crucial for identifying potential security gaps and ensuring that the organization’s infrastructure is secure. A good article to give you more insights on ITAM is located here.
This standard focuses on software asset management. SMBs can benefit from adopting ISO/IEC 19770-1 by ensuring proper licensing, reducing the risk of unapproved software installations, and enhancing overall cybersecurity posture.
For more information on ISO/IEC 19770-1 go here.
While SOC 2 certification is often associated with larger enterprises, SMBs can leverage its principles for securing customer data and building a robust cybersecurity foundation. Emphasize areas like data protection, availability, and confidentiality.
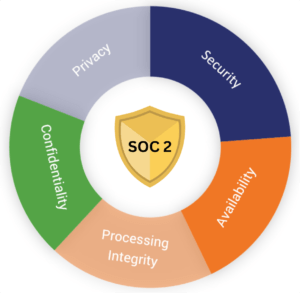
More information on SOC 2 can be found here.
For SMBs lacking dedicated cybersecurity experts, investing in training or consulting services from CISA-certified professionals can provide invaluable insights. CISA-certified individuals possess expertise in auditing information systems and ensuring their security.
More information can be found here.
SMBs can benefit from the simplicity of the NIST framework by aligning their cybersecurity efforts with its five functions. The framework provides a roadmap for identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents.
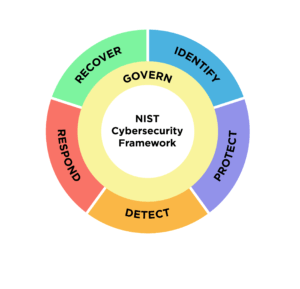
Find more information about NIST here.
Staying informed about CVEs allows SMBs to address known vulnerabilities promptly. Regularly monitoring and patching systems based on CVEs mitigates the risk of falling victim to exploits targeting known weaknesses.
More information on CVEs can be found here and here.
Developed by the Australian Cyber Security Centre, Essential Eight provides a prioritized list of strategies to mitigate cybersecurity risks. SMBs can use this as a practical guide to enhance their security posture.
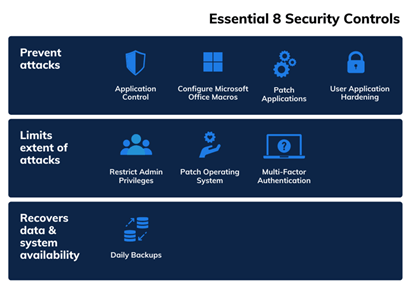
More information can be found here.
In the complex world of cybersecurity, SMBs can navigate the challenges by understanding and implementing relevant frameworks, certifications, and regulations. By adopting cost-effective measures like patching, ITAM, and leveraging the expertise of certifications like CISA, small businesses can build a robust defense against cyber threats. Remember, these efforts not only protect sensitive information but also serve as valuable assets when dealing with insurance companies, showcasing a commitment to cybersecurity that can positively impact risk assessments.



