
This is a companion blog to the “The SafeHouse” podcast dated September 26, 2024, with host Jeff Edwards, Co-Chair of the SafeHouse Initiative and his guests Angelika Mayen and Beau Butaud, Co-Founders of Render Compliance and SOC Champions.
In today’s digital landscape, where data security is paramount, understanding the Service Organization Control (SOC) standards is crucial for businesses. This blog post delves into what SOC 2 is, why it matters, and how organizations can leverage it to enhance their security posture.
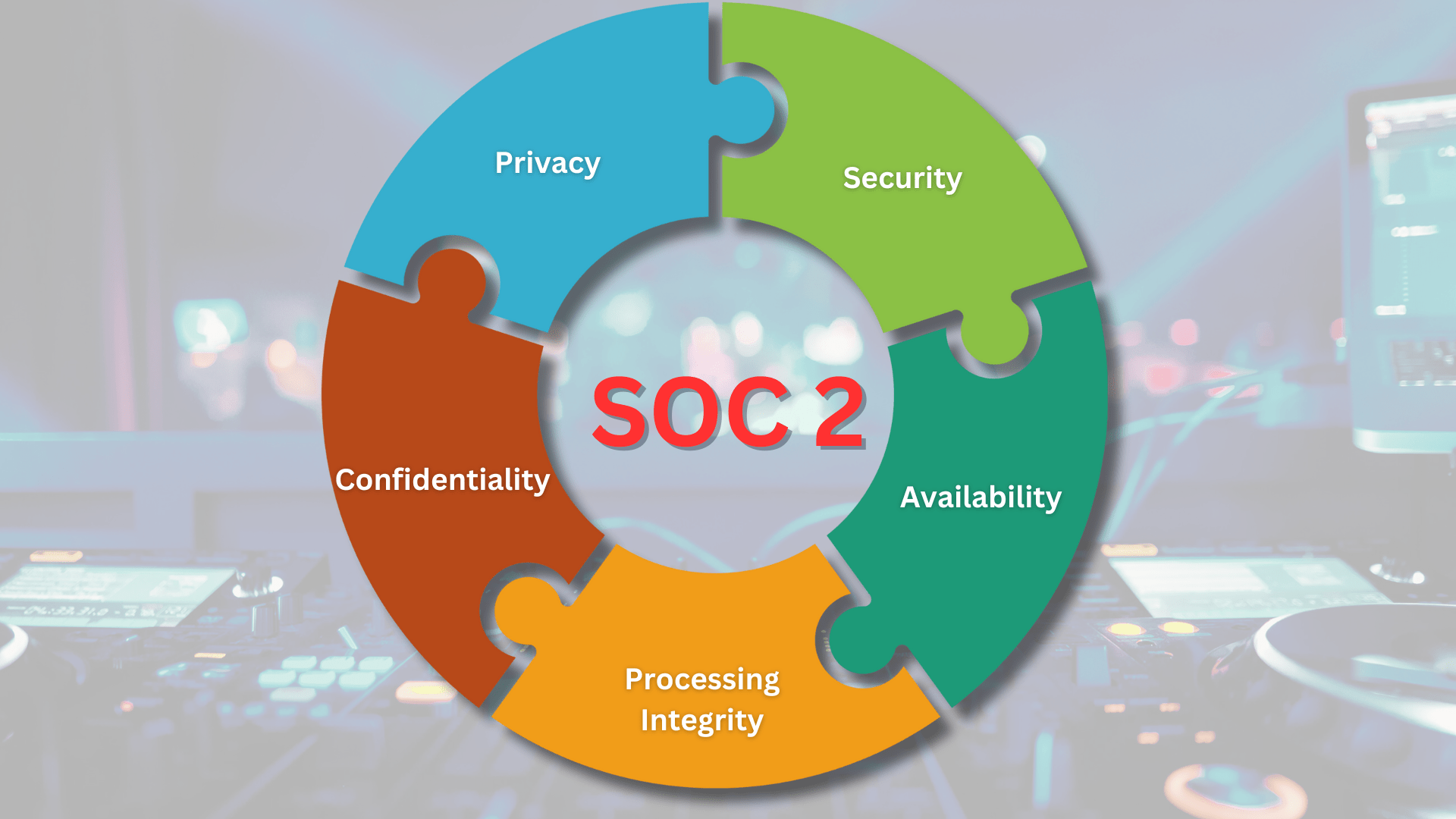
SOC 2, or Service Organization Control 2, is a framework developed by the American Institute of CPAs (AICPA) that focuses on the controls related to security, availability, processing integrity, confidentiality, and privacy of customer data. Simply put, it serves as a report card for organizations, showing how well they protect sensitive information.
The SOC 2 report is created by external auditors and includes a detailed examination of a company’s data handling practices. It is not a pass or fail assessment but rather an opinion on whether the organization meets the required criteria. The report typically spans at least sixty pages and provides insights into the company’s security posture.
There are three main types of SOC reports:
SOC 2 compliance is increasingly becoming a necessity for businesses, especially those that handle sensitive customer data. Here are some reasons why SOC 2 is crucial:
Implementing SOC 2 involves several key steps:
During the audit process, several key questions are typically addressed:
There are two types of SOC 2 reports:
Achieving SOC 2 compliance offers numerous advantages:
While the benefits are clear, obtaining SOC 2 compliance can be challenging. Common hurdles include:
SOC 2 compliance is no longer optional for businesses that handle sensitive data. It not only helps organizations build trust with clients but also enhances their overall security posture. By understanding the SOC 2 framework and actively working towards compliance, companies can position themselves as reliable partners in an increasingly data-driven world.
For any business looking to improve its security practices, starting with a SOC 2 report is a strategic move. Engaging with experts in the field can provide valuable insights and facilitate a smoother compliance process. Remember, data security is not just about compliance; it’s about protecting your clients and your business.
Readers Note: Be sure to visit the Contributor Tools page on the SafeHouse Initiative website for some helpful SOC 2 tools provided by our guest Render Compliance. Link -> https://safehouseinitiative.org/contributor-tools/



